NAT itu terbagi 2, Statis dan Dinamis
Tipe2 dari Statis dan Dinamis juga banyak…kita bahas satu2
==============================
Important Keyword


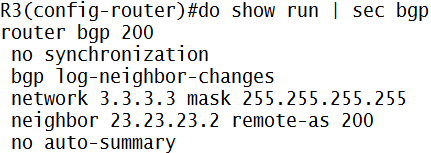
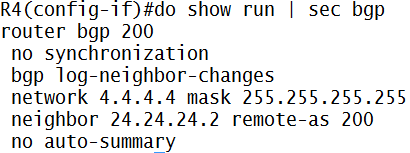
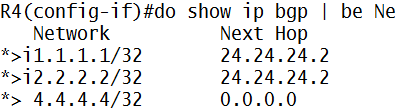
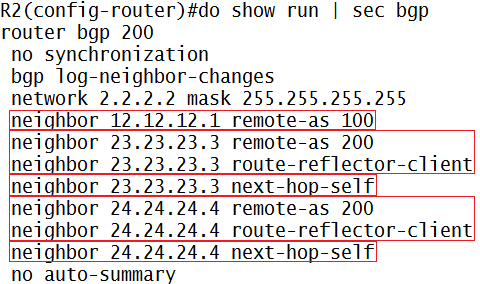
Kita bikin di interface loopback1 “ceritanya” ada LAN, pake keyword secondary, jadi ada 3 ip di satu interface (harus 1 network yah IP-IP secondary nya)
Trus ip route ke loopback R2, pake default route aja


Nah…important keyword dalam implementasi NAT adalah ip nat inside/ip nat outside
Di interface loopback1 (ato interface yang mengarah ke LAN Network) kita ketik ip nat inside, supaya si R1 tau…ini IP yang mau ditranslate
Di interface fa0/0 kita kasi ip nat outside, supaya R1 tau…ini interface tempat hasil translate-an IP nya
Kadang mudahnya gini:
- Di suatu interface yang kita “mark” ip nat inside…tandanya itu Interface yang mengarah ke Network Local/LAN (Private IP)
- Klo di interface itu kita “mark” ip nat outside…berarti interface ini tempat IP Public…mengarah ke WAN/ISP
===========================
Static NAT
1:1 Translation (1 buah IP di translate/dirubah ke 1 buah IP lainnya)
Di R2 juga sama, sekarang kita liat konfigurasi Static 1:1 translation
nya dibawah ini

Konfigurasi diatas artinya…”woi router…interface yang gw “mark” ip nat inside tolong mentranslate/rubah ip 1.1.1.1 ke 12.12.12.11 (ato 1.1.1.2 ke 12.12.12.2)”
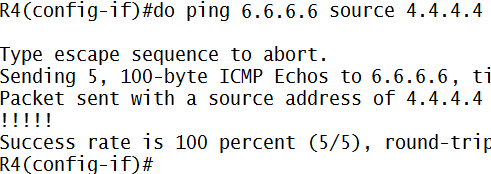
Coba kita ping (pake source yah…jadi ceritanya kita ping dari LAN kita, klo ping dari routernya sendiri ga akan dapet NAT-nya)

Nah..kita bisa liat…IP 1.1.1.1 (Inside Local) di translate ke 12.12.12.11 (Inside Global)
Begitu pula IP 1.1.1.2 ditranslate ke 12.12.12.12
Apaan sih Inside Global dan Local serta Outside Local dan Global?!
- Inside Local = IP yang terdapat di interface yang sudah di mark “ip nat inside”
- Inside Global = ini yang di mark “ip nat outside”
- Outside Local = biasanya IP tetangganya (directly connected neighbor)
- Outside Global = biasanya tempat tujuan berada
IP to Interface IP (Mapping 1 buah IP ke IP Interface)

Ini artinya “tolong translate IP berikut ini (1.1.1.1/1.1.1.2) ke IP yang ada di Interface fa0/0”

Nah…diatas kita coba ping dari 1.1.1.1 trus dari 1.1.1.2, yang keliatan adalah IP yang terakhir kali nge-ping (1.1.1.2, IP 1.1.1.1 sudah di delete dari nat translation-nya)
Pool Network to Pool Network (define network untuk ditranslate lalu define network hasil translate)
Lebih fleksibel, configurasinya lebih ga ribet (daripada kita harus define 1-1 ip yang di translate…mending define “range” ip nya aja)

Ini artinya “tolong tanslate network 1.1.1.0 ke network 10.0.0.0 dengan prefix /24”

Verifikasinya tinggal liat gambar diatas
Static Extendable (1:2 translations)
Jadi 1 IP ditranslate ke 2 IP atau lebih

Ini artinya “tolong translate 1.1.1.1 ke ip 10.1.1.1 ATAU 20.1.1.1“, dengan keyword extendable
Ketika R2 mau mengakses 1.1.1.1, dia bisa pake 10.1.1.1 ato 20.1.1.1, contoh kita mo telnet dari R2 ke R1:

Create telnet dulu, trus coba telnet ke 10.1.1.1 dan 20.1.1.1 (untuk ke 1.1.1.1)

===================================
Dynamic NAT
ACL to Range IP (IP yang mau di translate di filter dulu oleh ACL trus di translate ke pre-defined range IP)

Konfigurasi diatas maksudnya “tolong translate IP-IP yang ada di pool DINAMIS ke IP 12.12.12.11 sampai 12.12.12.13 dengan prefix /24”
Create juga pool dan ACL nya yah (jangan lupa)

Hasil nat translation-nya bisa di lihat diatas
Reverse ACL to Range IP (klo tadi yang di translate adalah ip nat inside source, sekarang ip nat inside destination)

Tipe NAT seperti ini berguna klo ada traffic dari luar mau masuk, untuk telnet router kita misalnya
Tentu IP yang mau telnet itu harus diizinkan dulu (baca: dipermit ACL) untuk di translate ke IP Local

Pada gambar diatas..R2 telnet dengan menggunakan IP 12.12.12.11 dan di translate ke IP 1.1.1.1 (“show ip nat tr”-nya dibawah)

NAT Overload (IP ke Interface)
Nah…biasanya kita pake ginian nih, ini tipe NAT paling populer

Disini maksudnya “tolong translate IP-IP yang di permit oleh ACL nomor 1 ke IP yang ada di Fa0/0”
Overload = cek article NAT gw tentang overload (also known as PAT – Port Address Translation)

Kok sama ya…kek yang di static? Ya memang…yang membedakan statis dan dinamis adalah cara router memilih IP mana saja yang mau ditranslate (static = input sendiri, dinamis = pake ACL/Pool)
NAT Overload (IP ke Pool IP)
Like the name said…sama2 overload…tapi IP yang “lolos” dari ACL akan di translate ke Pool IP yang sudah disediakan
Contoh configurasi:

Untuk nge-tes nya…kita harus bareng2 dari 2 komputer (misalkan) ping ke R2…baru di show ip nat tr
===============================
Dual NAT
Will be updated soon…
NAT Load balancing (salah satu contoh dual NAT)