Kemaren kita bahas tentang salah satu varian Cisco VPN, yaitu DMVPN
Sekarang kita bahas tentang varian lainnya, yaitu VTI (Virtual Tunnel Interface)
Pre-requisite:
- GRE (knowledge about DMVPN dan Secure DMVPN much preferred)
———————————————————————
Why VTI?
Kelemahan dari DMVPN adalah dalam pemakaian tunnel-nya, klo kita mau konek ke branch, kita pointing ke IP tunnel-nya (tul gak?!?), bikin IP baru lagi dong (taro di tunnel), dan yang pasti management IP lebih berat lagi dong, belum lagi ga terlalu “routable” itu IP di tunnel (fungsi IP tunnel-nya itu kan buat konekin tunnel satu ke yang lain…itu tok)
Nah, kelemahan ini yang VTI eliminasi, di interface tunnel ga perlu ada IP, pointing tunnel-nya ke IP “beneran” (biasa ke loopback)
Kok bisa? Lets take a look at the network diagram and configuration below
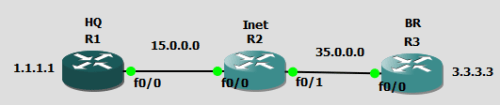
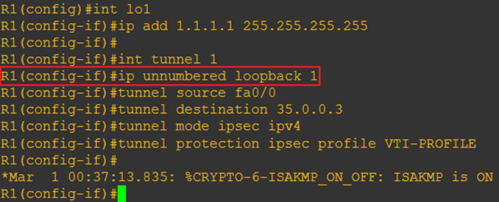
Take a look at “int tunnel 1” with no ip address and replaced by “ip unnumbered loopback 1” command alias R1 akan pointing IP Address tunnel-nya ke loopback
Untuk maksud “tunnel mode ipsec ipv4” dan “tunnel protection ipsec profile [nama]” sudah dijelaskan di Secure DMVPN (artinya lu harus setting sendiri profile-nya…liat aja caranya di link yang gw kasih)
Untuk routing bisa sendirilah…gw pake default route aja
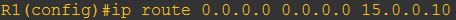
Lets verify is VTI tunnel kita dapet IP apa engga
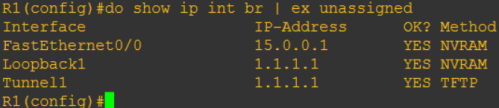
Take a look at IP address Tunnel1…IP-nya adalah 1.1.1.1, method TFTP…artinya VTI Tunnel kita dapet IP
Lets ping to the R3 tunnel (which is 3.3.3.3)
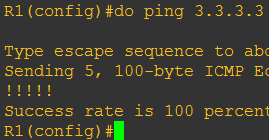
Done…
——————————————————-
Bonus…
Advantages of VTI
Karena kita pake interface “beneran” (yang IP-nya routable), berarti kita juga bisa taro QoS di VTI
Contohnya…klo ada traffic make IP loopback untuk koneksi normal kita kasi precedence 4 (semakin tinggi nilai semakin di prioritaskan), sedangkan klo ada traffic make IP looback buat VPN-an kita kasi precedence 2 (that’s great!!!)
Nyok kita liat…
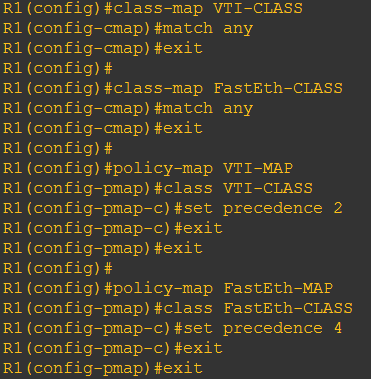
Bikin Klasifikasi Traffic (Class-map) dulu …untuk misahin traffic biasa (FastEth-Class) dan traffic VTI (VTI-Class)
Trus bikin Policy untuk masing2 traffic (Policy-map), lalu taro de di interface tunnel dengan service policy output [nama policy-map] seperti yang kita lihat dibawah ini
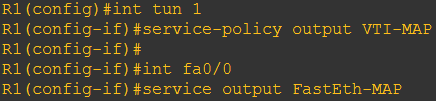
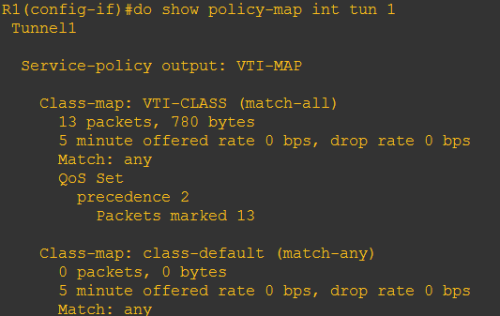
Nah, klo trafficnya pake VTI Tunnel (buat ke branch misalkan), nanti akan di kasi prioritas rendah (precedence 2), sisanya normal
Untuk lebih jelas tentang Traffic Classification, Traffic Policing, dan Traffic Shaping bisa dilihat disini
Verifikasi:
———————————————
References:
VPN Differences @Ciscozine.com – http://www.ciscozine.com/ipsec-vpn-ezvpn-gre-dmvpn-vti-getvpn/
Comparing VPN @Firewall.cx – http://www.firewall.cx/cisco-technical-knowledgebase/cisco-services-tech/945-cisco-comparing-vpn-technologies.html
Advantages using VTI by Paul Stewart #26009 (Security) – http://www.packetu.com/2012/05/01/avantages-of-using-svti-based-vpns/
Advantages using VTI @Cisco Support Forum – https://supportforums.cisco.com/blog/149426/advantages-vti-configuration-ipsec-tunnels
IPSec WAN Design Review @Cisco whitepaper – http://www.cisco.com/application/pdf/en/us/guest/netsol/ns171/c649/ccmigration_09186a008074f22f.pdf